Managing users via Directory Synchronization¶
Attention
This feature currently requires a user with System Administrator privileges. It will become available for other privilege levels in a later release.
ad-connect users from a local user directory can be integrated seamlessly into Kopano Cloud.
Create new sync configuration¶
A synchronisation configuration defines how the system should synchronise directory information, such as users from an external source, an Active Directory or an LDAP server. To identify a new set of synchronisation configuration settings, start by selecting a name. It is recommended that you choose something unique, such as the name of the synchronisation server.
To add a new synchronisation configuration, please follow the instruction shown below, and on your screen:
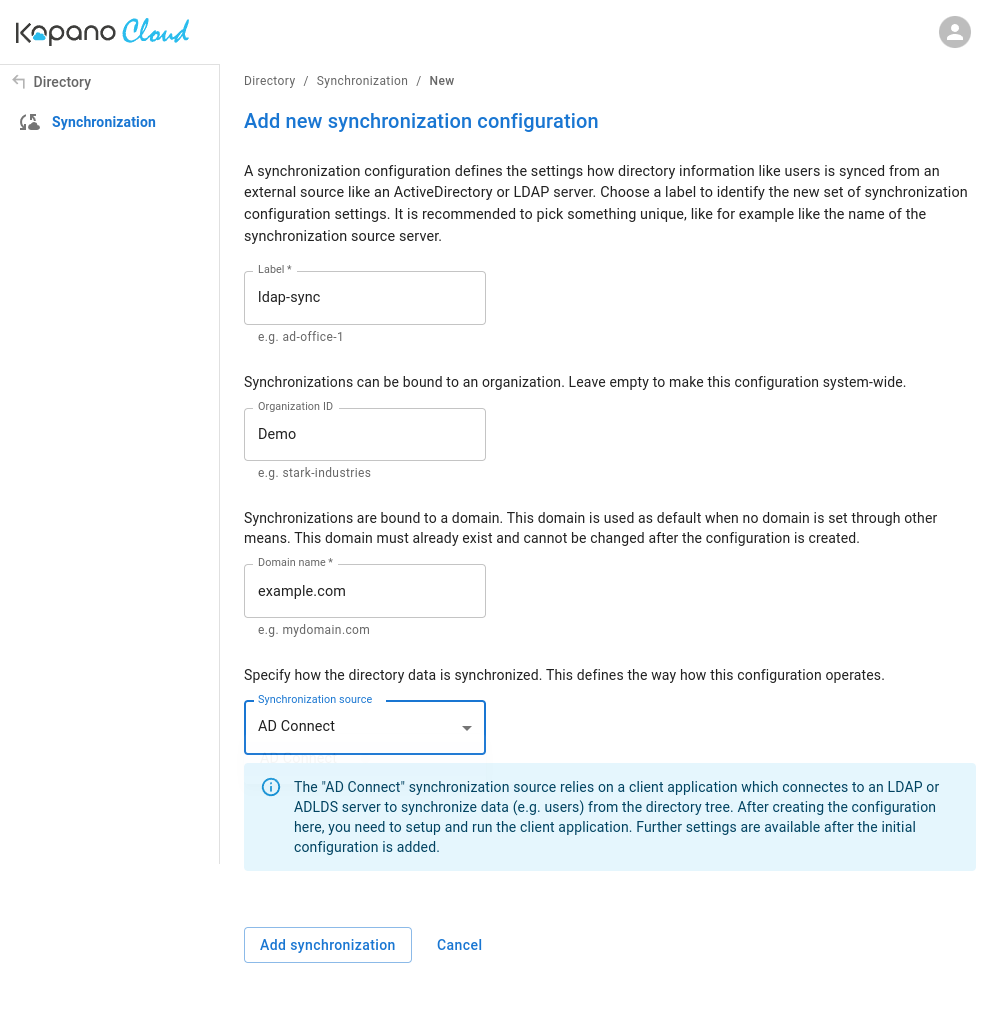
After inputting all settings, please click on . This will prompt the system to present you both with the Application ID and Secret Token.
Important
Please take note of the secret, as it will only be shown once.
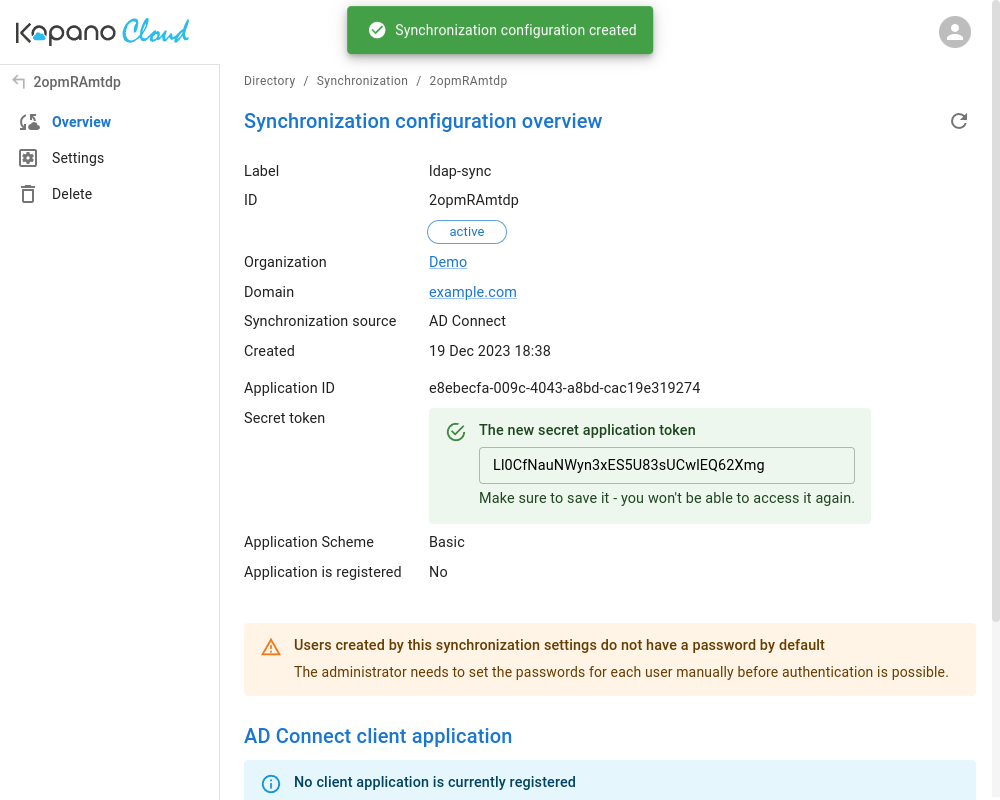
The synchronisation configuration overview page shown below, provides you a download link for ad-connect, and is able to show whether a client is currently connected or not. The client download archive contains a binary, which includes a sample configuration and a readme file, containing further instructions.
Configuring ad-connect¶
To configure ad-connect, please modify the example adc.yaml, to match your environment. An example of this, is shown below:
settings:
dry-run: true
no-update: false
no-create: false
no-delete: false
delete-disables: true
no-update-provider-mismatch: true
create-as-disabled: false
backend:
ldap:
addr: ldap://your-ldap-server.local
bind_dn: cn=readonly,dc=lg,dc=local
bind_password: readonly
base_dn: dc=lg,dc=local
scope: sub
sync:
page_size: 20
filter: (objectClass=inetOrgPerson)
authentication:
username_attribute: mail
username_filter_template: (&(objectClass=inetOrgPerson)(mail=%s))
timeout: 5
A note regarding the settings part in adc.yaml
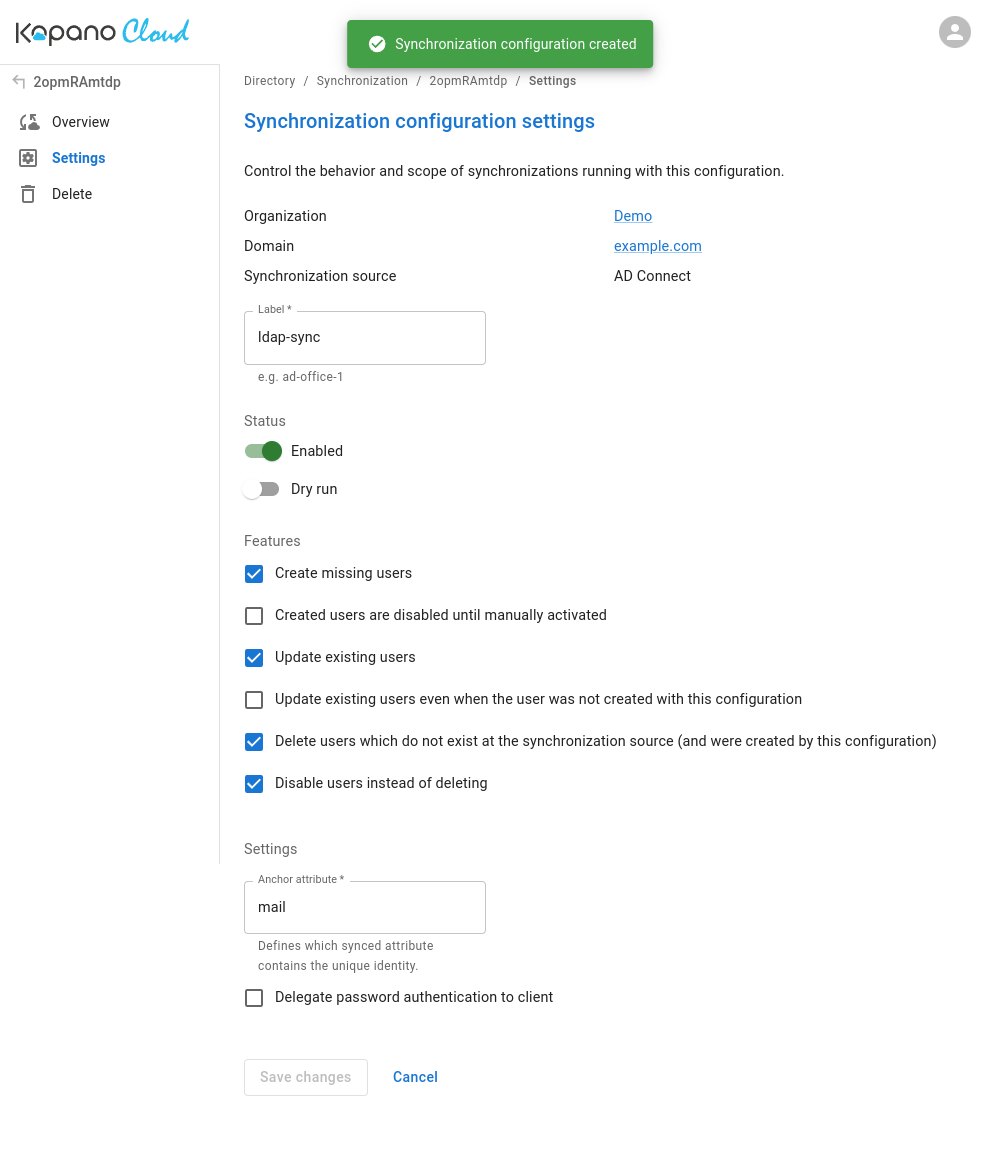
As defined in the synchronization configuration settings, it is possible to define these settings both on the server, and client side. If the configuration contains values that conflict with one another, the server will override the client's settings. (e.g. If the server only allows dry runs, the client will unable to import users into the server)
Running ad-connect¶
ad-connect has two modes of operation.
1. When called with the imp parameter, it imports users from the configured LDAP source.
2. When called with the run parameter it connects to Kopano Cloud.
When password delegation is enabled, the client is required to be connected at all times, to allow users to sign in.
Systemd service setup example¶
To run ad-connect with systemd, there are a few requirements.
First you need to create a new service configuration file called adc.cfg, and save it in /etc/e4a-ad-connect.
The adc.cfg file needs to contain the following:
AD_CONNECT_ADDR=address-of-server:443
AD_CONNECT_AUTH=application-id:secret-token
AD_CONNECT_CONFIG=/etc/e4a-ad-connect/adc.yaml
To create the actual service:
- run
sudo systemctl edit --force --full systeminfo.service - Then add the following content to the service file:
[Unit]
Description=ad-connect
After=network.target
[Service]
Type=simple
User=nobody
Group=nogroup
WorkingDirectory=/etc/e4a-ad-connect
ExecStart=/usr/local/bin/adc run
EnvironmentFile=/etc/e4a-ad-connect/adc.cfg
ExecReload=/bin/kill -s HUP $MAINPID
ExecStop=/bin/kill -s TERM $MAINPID
Restart=always
RestartSec=10
TimeoutStopSec=30
KillMode=process
[Install]
WantedBy=multi-user.target
Note
Installers for Windows and Linux systems and an OCI container, will be made available in a later release.
What kind of information can I import with ad-connect?¶
By default, ad-connect with use the following attributes when creating/updating a user:
cnordisplaynametitledescriptionmobiletelephonenumbermail
When in the Directory Synchronization Settings the option Sync aliases when users are created, updated or deleted is unchecked, the ldap mail attribute needs to be unique.
Anchor attribute¶
The anchor attribute can be modified in the "synchronization configuration settings". The anchor attribute defines which attribute should be used as the unique property of a user. If the unique property is a valid email address, then it will be used as such. Otherwise, a domain will be mapped to it depending on the location within the LDAP tree. An example of this can be seen below:
[..]
domain_map:
dc=lg,dc=local: ad-connect.local
[..]
Important
The mail attribute has been the anchor attribute on the server side, up until version 6.1.2. From version 6.2.0 onwards the anchor attribute is uid.
Attribute mapping¶
If important information is stored under another attribute, it is possible, during runtime, to map it to the correct attribute. This can be seen, in the example below. Here the value of kopanoAliases is treated as the mail attribute, remapping its value.
[..]
attributes_map:
kopanoAliases: mail
[..]
Alternatively, it is also possible to transform attributes, when reading data from the LDAP. This is useful when, for example, the LDAP contains a different domain to the name associated with the LDAP attribute.
[..]
attributes_transformer:
mail: 's/\(.*\)@.*/\1/'
attributes_transformer_command: "sed --sandbox -e"
[..]